CYBER SECURITY CONSULTANCY SERVICES
CYBER SECURITY CONSULTANCY SERVICES
Cyber security is no longer a fringe concern. In 2023, almost a third of businesses in the UK reported breaches or attacks. As a leading cyber security consultancy provider, we understand the daily threats posed to businesses, as well as how to manage them.
We provide a suite of expert services to protect your business and clients from what are now very real cyber threats.
- Turnkey Cyber Security
- Expert Testing & Consultancy
- Spot & Eliminate Vulnerabilities
- Train Your Staff
- Ensure Compliance With Changing Regulations

78% Average First Contact Resolution
98.8% Average Customer Satisfaction Score
Rapid Response Time
Cyber Focused Approach
Services
Our Cyber Security services
Despite the blatant and growing risks, just three in ten businesses have performed a cyber security risk assessment.
We are one of the UK’s most dedicated cyber security service providers, driven by a mission to reduce the impact of cyber crime. Alongside our advanced IT services, we offer a comprehensive roster of cyber security services designed to keep your business safe, protecting your interests and those of your customers.
Our award-winning cyber security consultancy services can be provided individually or as a completely turnkey package, bolstering your defences and helping to keep you safe online.
Penetration Testing
A key tenet of our cyber security consultancy is helping you identify flaws in your existing protections – chinks in your armour. Backed by accreditation from the Council of Registered Ethical Security Testers (CREST), our penetration testing will deliberately attempt to poke holes in your cyber security to spot weaknesses and help you address them before an attacker does the same!
We’ll assess your systems in their entirety, including on-site equipment, user devices and cloud-hosted systems.
Speak to our expert team today to book your cyber penetration testing.
Fully Managed Cyber Security
Complete cyber security coverage, with all facets of digital security taken care of. The Optimising IT team will independently manage and maintain your entire cyber security system. Our service promises total peace of mind and state-of-the-art protection.
Cyber Security Review and Audits
The first step in implementing effective cyber security is identifying strengths and weaknesses, so you know where to allocate resources. As a comprehensive cyber security service provider, we can conduct a thorough, in-person audit of your entire system in line with best practices laid out by ISO 27001 and Cyber Essentials.
One of our experienced security consultants will visit your site and thoroughly evaluate your security governance strategies, network and systems security and conduct a vulnerability analysis of your internal networks. They’ll then issue you with a user-friendly report outlining their findings and recommendations, with actionable, in-depth technical data available for your IT team.
For your cyber security audit, speak to our team today.
Cyber Essentials and Cyber Essentials Plus
You’ve got your cyber security sorted – great! You’re a step ahead of most businesses in the UK, but how do you prove it to concerned clients? That’s where Cyber Essentials and Cyber Essentials Plus approval comes in.
The Cyber Essentials verifications are government-designed and backed accreditations that verify the integrity of your digital defence systems and act as a reassurance for potential clients. Accreditation also entitles any business with an annual turnover of less than £20 million to automatic cyber liability insurance.
At Optimising IT, we can work with you to get your defences up to scratch before having your systems assessed and certified, as well as providing long-term support to keep you compliant.
To kickstart your road to being Cyber Essentials certified, just drop us a line.
Cyber Security Training For Employees
Research shows that 82% of data breaches involve human error. Even if you think your cyber security is completely airtight, your employees can fall victim to tactics such as phishing emails and social engineering scams.
We can deliver comprehensive, expert-informed cyber security training for your employees, helping to plug a considerable gap in your cyber defences. Our training team is made up of Certified Information Systems Security Professionals (CISSPs) – a coveted accreditation from the International Information System Security Certification Consortium (ISC)2, recognised by the US Department of Defense and the ANSI National Accreditation Board.
Learn more about our cyber security training here.
Cyber Security Consultancy
Our consultancy service offers a broad and bespoke view of your cyber security process. Tailored to your unique requirements, we’ll provide guidance, support and expertise across all areas of cyber security.
From technical training and security architecture design to breach investigations and cyber attack recovery, our cyber security consultancy covers anything and everything you could ever need.
About cyber security
What exactly is cyber security?
In a little over twenty years, the internet has changed the way we conduct our daily lives, both at home and at work.
The mention of the word “cyber” is enough to conjure up images of hooded attackers, typing commands on a keyboard at 2 am, and with the amount of press coverage in mainstream media, you would be forgiven for thinking everyone knows everything about it.
Keep up-to-date with our Cyber blog news updates, providing current, pragmatic Cyber-security advice. You can also find out how our cyber-security consulting services are helping our clients to manage and reduce their cyber risk on our case studies page.
Download our useful Cyber-security Consultancy & Strategy service summary for more detail.
“Cyber” is nothing more than a great marketing term, used to brilliant effect to describe what is a complex and deep subject area. Cyber encompasses many things, but when we think about it in the context of preventing cyber-attacks, we’re talking about information security.
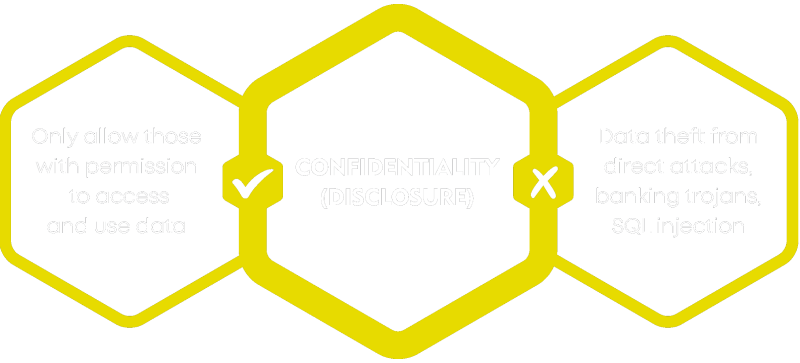
Information Security is the art of protecting the confidentiality, integrity and availability of information. The inverse is what we’re trying to prevent; the disclosure, alteration or destruction of data.
UNDERSTAND YOUR RISKS
At its core, good Information security practice is based on quality risk management. The best place to start is understanding what your organisation risks are, then putting in place appropriate controls to reduce that risk. You can’t ever protect yourself 100%, but you can take practical and pragmatic steps to limit cyber-threats to your business, and it doesn’t need to cost you the earth.


About our Cyber services
Cyber penetration testing
Much like an MOT on your car, regular testing of systems is key to identifying known security weaknesses and addressing them, before the attackers can take advantage.
Cyber Penetration testing takes care of the technical testing of your environment across on-premises, user devices and cloud hosted systems.
We can provide penetration testing, one-off or ongoing vulnerability scanning services, technical security reviews or any combination to suit your needs:
- Internal and external infrastructure penetration testing
- Web application cyber penetration testing
- Regular Internal and external vulnerability scanning
- CREST accredited Cyber Penetration testing
- Rates at up to 40% less than the competition

About our Cyber services
Cyber essentials and Cyber essentials Plus
You have cyber covered, but the first question on the latest tender asks what external security governance you have.
Cyber Essentials and Cyber Essentials Plus
Cyber Essentials is the UK government-approved baseline Cyber Security standard, administered by https://iasme.co.uk/
Optimising IT provides full Cyber Essentials and Cyber Essentials plus services including:
- Cyber Essentials gap analysis
- Vulnerability scanning
- Remediation projects to get you in shape to meet the requirements
- Ongoing pro-active services to keep you compliant
Get in touch to find out how you can benefit from our Cyber and Information Security Compliance services and reduce cyber-risks to your business.



About our Cyber services
Cyber security reviews and audits
A comprehensive cyber-security review, based on ISO27001 principles and including a gap analysis against Cyber Essentials Criteria.
You know you need to do something about cyber-security, but where do you start? The first step in any journey is understanding where you are. In the context of cyber security, understanding where your risks are right now, and importantly, what you need to do to reduce those risks is the first step on your cyber-security journey.
Our Cyber Security service provides your organisation with a real-world view of how your current security approach stacks up against standards like Cyber Essentials and industry best practice. Crucially, it also provides key advice about what actions to take to safeguard your business.
One of our highly skilled and experienced consultants will spend up to a day onsite with your organisation, evaluating areas including:
- Security governance
- Network and systems security
- A vulnerability scan of your internal networks to identify any known security issues, including common configuration issues and missing security updates
DETAILED REPORTS
We’ll provide a focussed report detailing key areas for improvement as well as the actions required to improve your current Cyber Security stance. The output from the vulnerability scan will be presented in a management friendly report, with the detail available for your technical teams.
Get in touch to find out how you can benefit from our Cyber Security services and reduce cyber-risks to your business.



About our Cyber services
Cyber security training
Cyber is the number one risk to UK businesses, with 95% of cyber-attacks starting with an employee being tricked.
Cyber security awareness training
Your staff are the biggest chink in your armour when it comes to cyber-security, with over 92% of malware delivered via email. You can put multiple locks on the door to protect your data, but without appropriate staff training on passwords, data handling and identifying phishing emails, you may end up giving away the keys to the castle.
Proactive Prevention
As a professional cyber-security consultant, we believe that prevention is better than cure. With that in mind, we have developed a flexible, comprehensive cyber-security half-day training workshop for both business leaders and employees, which we continually update to incorporate the latest cyber-attack threats and trends. We also tailor our content for each business, as the nature of cyber-threats can vary depending on the services and industry you operate in.
Expert Accredited Trainers
Our experts are Our experts are Certified Information Systems Security Professionals (CISSP) accredited and have a wealth of knowledge and experience. They also continue to help protect businesses, working with them to implement protective measures and develop ongoing cyber-security strategies. It’s fair to say that they live and breathe cyber-security.
Why is training important?
An increasing number of businesses are benefiting from proactive prevention to the daily cyber-security threats targeting any size organisation. Staff are the number one risk, as they have easy access to your systems and data. Therefore, training your team is one of the best preventive measures, with minimal investment needed and a lot to gain to protect your data. With 60% of SMEs that suffer a major cyber-attack ceasing to trade within six months, make sure you’re doing everything you can to avoid being another statistic.
Cyber Security Training Workshops
We offer both our standard user awareness and bespoke training, tailored to deliver the most relevant and up-to-date content, focussing on the cyber-threats facing your business and industry. One of our expert trainers will discuss this with you before the training day, making our training flexible to fit with your business needs.
Half-day Training for Business Leaders:
Good cyber-security practice requires your organisation to have a culture of security, driven from the top. All too often, cyber-security is seen as the responsibility of the IT department. Join us for our practical cyber workshop, where you’ll learn about how to approach cyber in the right way, with a risk management led approach.
Half-day Training for Employees:
Our Cyber Awareness Training Workshop is aimed at organisations of all sizes and delivered in a workshop format, covering a series of real-world examples and exercises. It’s designed to be informative and engaging to reinforce learning. The training covers why and how hackers target organisations, the techniques they use and most importantly, how we can alter our behaviours to be more aware of the threat and reduce the likelihood of it happening to us. All content is regularly refreshed to reflect new and emerging threats.
We Cover the Following Format:
About our Cyber services
Fully managed cyber security protection
Everything you need to help safeguard your business from cyber-threats.
Managing cyber-security can be a daunting, exhaustive full-time job. With growing demand and a largely static skills base, the cost of employing appropriately skilled and experienced cyber-security staff is increasing.
Our cyber security offering
- Initial review and get fit activities — allowing you to understand your current security status and plan to improve.
- Managed governance, risk and compliance activities.
- Ongoing technical security management across your entire Information systems portfolio.
- Regular technical testing (managed vulnerability scanning).
- Annual pen testing.
- Managed patching.
- Managed anti-virus.
- Managed network security, including firewalls, web filtering, IPS, advanced malware scanning.
- 24x7x365 log correlation monitoring (SIEM), security operations, alerting and reactive security across your on-premise and cloud infrastructures.
And all of this too...
- Advanced email security.
- Two-factor authentication.
- Independent supplier security reviews and ongoing supplier management.
- Ongoing review and governance.
- Breach detection and Dark Web analysis – identifying a breach when it does occur, including scanning the Dark Web for stolen data and credentials associated with your business.
- External compliance assistance, including Cyber Essentials, Cyber Essentials plus, ISO27001 and PCI DSS.
- Security control remediation — we can assist by providing project expertise to resolve any identified security issues, e.g. system configuration and network changes.
- Staff Cyber Awareness Training — especially with over 92% of malware delivered via email.
About our Cyber services
Cyber security consultancy
Cyber is the number one risk to UK businesses, with 95% of cyber-attacks starting with an employee being tricked.
Get in touch with one of the UK’s most trusted cyber security service providers today and protect yourself, your staff and your clients from the evolving world of cyber threats.
While many organisations are just starting on their cyber journey, others are more mature and have specific requirements or gaps that require external expertise to fill.
As a cyber-security consultancy, we can provide a bespoke service to you, tailored to your specific needs with our Cyber Consultancy service:
- Information Security Management
- Virtual and fractional CISO services
- Staff technical training
- Security architecture design
- Requirement definition, tender review
- Staff selection services
- Due diligence/acquisition activities
- Breach investigation and forensics
- Breach response services



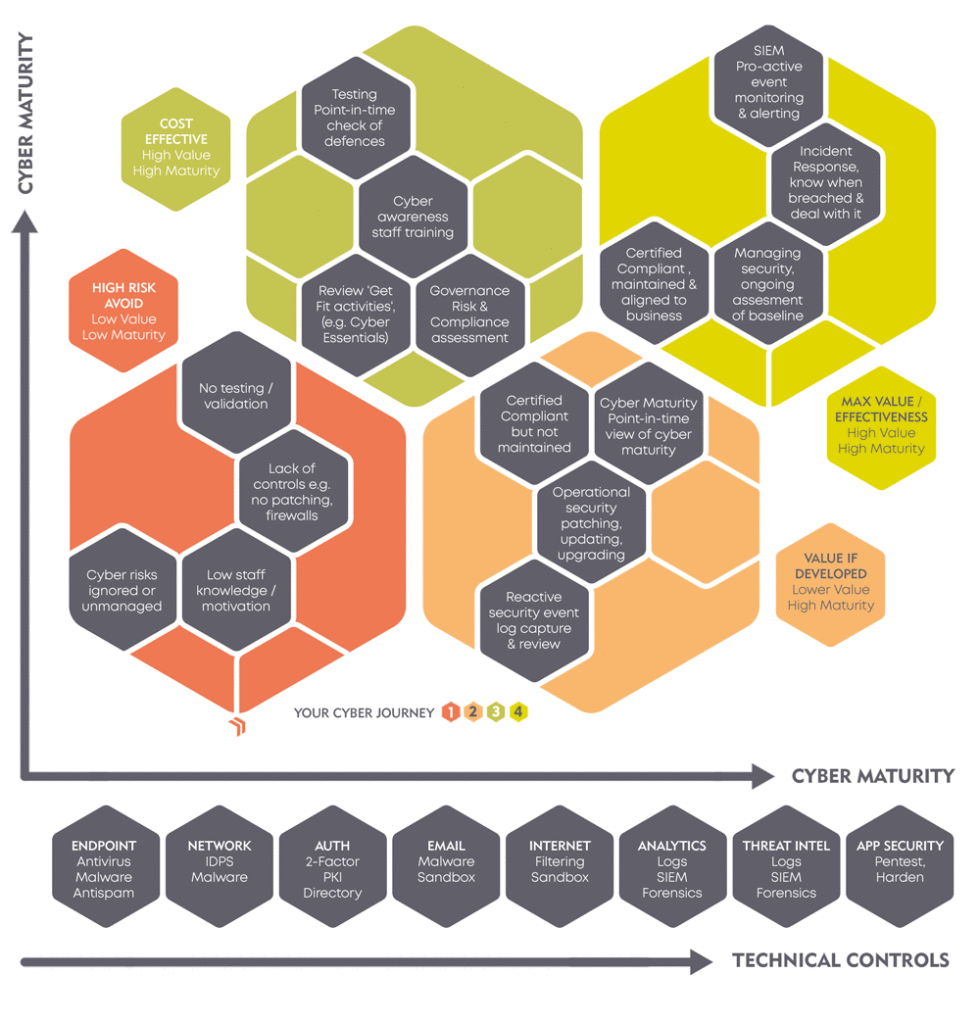
Are you ready?
How mature is your cyber security?

Services
Our other Services
Discover our full-service solutions














